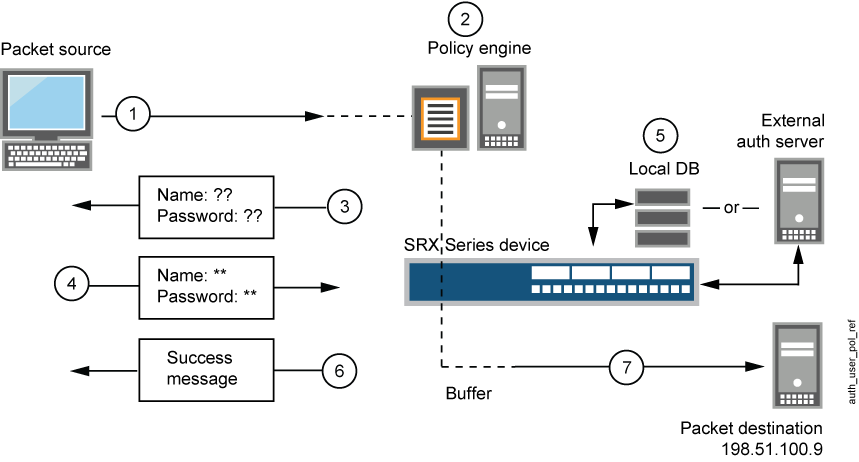
Figure 2 from Security enhanced IEEE 802.1x authentication method for WLAN mobile router | Semantic Scholar

The login method is configured on the VTY lines of a router with these parameters.. The first method for authentication is TACACS. If TACACS is unavailable, login is allowed without any provided
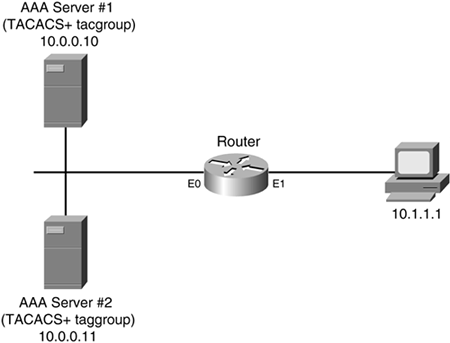
Authentication :: Chapter 5. Authentication, Authorization, and Accounting :: Part II: Managing Access to Routers :: Router firewall security :: Networking :: eTutorials.org






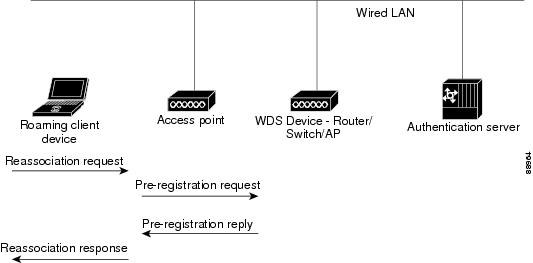
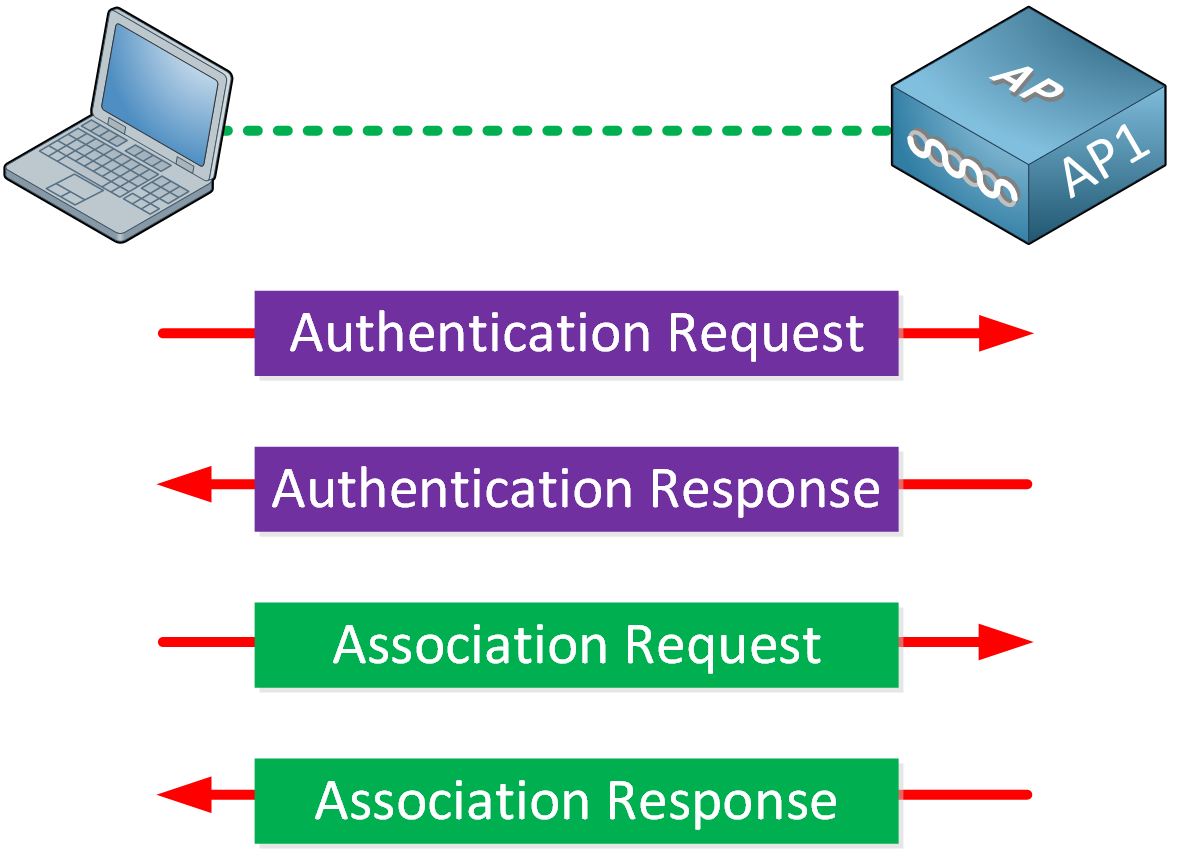
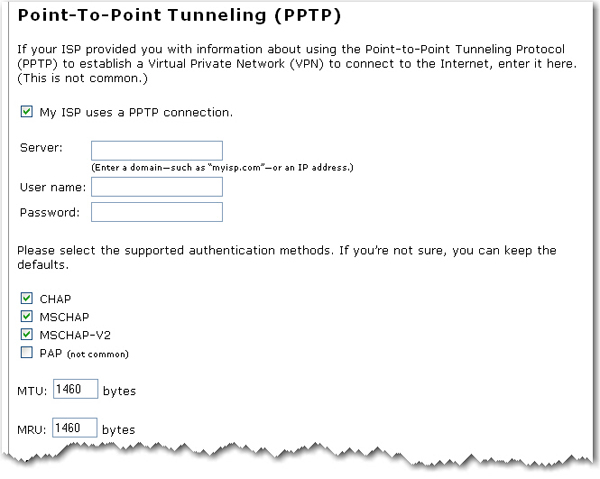
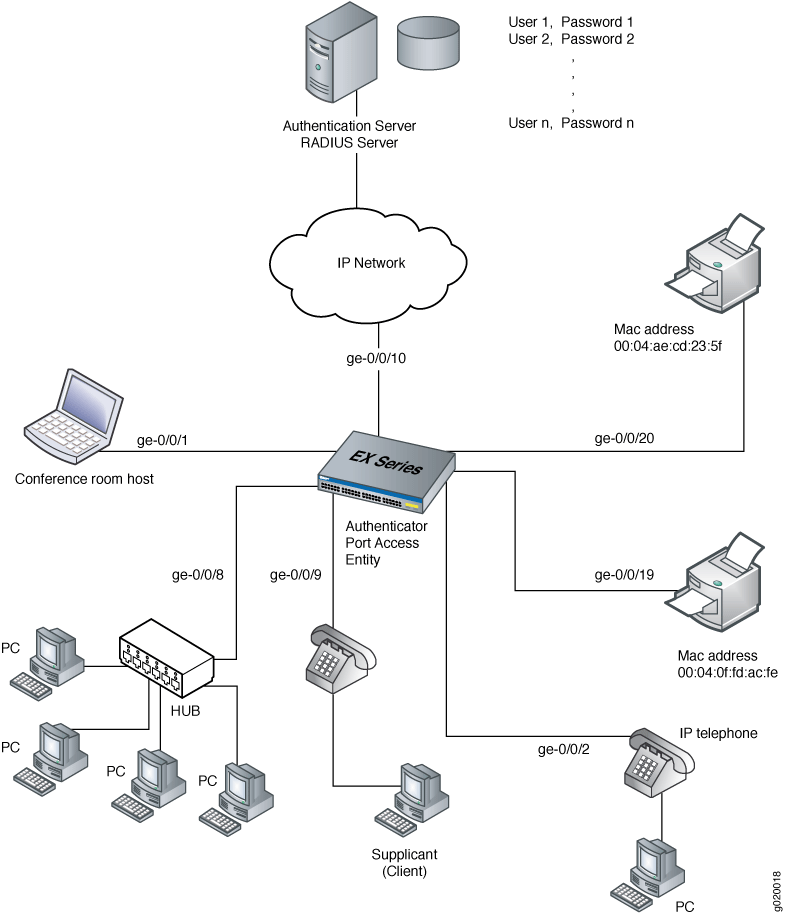
![PDF] A REVIEW OF 802.1X-EAP AUTHENTICATION FOR ENTERPRISE WLANS | Semantic Scholar PDF] A REVIEW OF 802.1X-EAP AUTHENTICATION FOR ENTERPRISE WLANS | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f18b24a0c90db8427a636381f9156ef53437eafe/3-Figure2-1.png)